How the Dialogue is Disconnected From Reality
Within the increasingly hot topic of health data privacy and security, we can find news and content that ranges from technological innovations (mostly security) to philosophical debate (mostly privacy). On occasion, we encounter a FOMO-triggering estimate of just how much our health data is worth (mostly questionable math).
From all walks of life, and across the political spectrum, Americans overwhelmingly seem to agree with the statement:
I should be able to control who can access my healthcare data.
Indeed, and I agree with this as well, but this statement isn’t exactly laying out a plan of action.
Data Security Versus Data Privacy
The management of data security is expensive, but it is not terribly mysterious. Better technology (more money); more redundant verification and access policies (more money); and better paid staff (more money), along with more money, generally will improve data security.
The path is not easy, but it is straightforward – practical guidance is plentiful.
The same cannot be said for health data privacy. We feel very strongly about data privacy – it is our unique health data, after all – but often struggle to explain why we feel the way that we do. It is challenging to attempt to quantify the value of privacy absent a breach.
There is some excellent writing on privacy within the interconnected health IT infrastructure[1],[2],[3]. Most of it comes to a similar conclusion: regulation should recognize the attributes of multiplicity, permanence, and the relational nature of data’s meaning, not merely the distinction between privacy and security. Importantly, these concepts are critical for truly informed decision making where opportunity for it exists.
Privacy Was Not the Impetus for HIPAA
When most people think of health data privacy law, they think of the Health Insurance Portability and Accountability Act (HIPAA), which passed at the federal level in 1996, with three main provisions. The Privacy Law, contained within the administrative simplification provision, was not actually finalized until 2002; its primary purpose was not actually data privacy, but rather, to promote the standardization of electronic health information in order to advance health outcomes research. The standards and safeguards in the data privacy piece were included because Congress recognized that facilitating data exchange could have the side effect of increased risk to the privacy of individuals.
In fact, the majority of comments received by the Department of Health and Human Services (HHS) from researchers were those urging them to exclude research data entirely from HIPAA and any associated Privacy Law[4].
States Enact Well-intentioned but Ineffectual Legislation
The states that have rolled out their own data privacy laws are adding fragmentation and complexity to an already confusing structure. Some of these laws require companies to provide an ‘opt-out’ mechanism to any resident who wishes to exercise it. It sounds great in theory, but there is no actual mechanism whereby all of your historic data can be tagged to self-destruct at the push of a button, for reasons that will be fleshed out in this writing. Furthermore, many of the laws have exemptions that would apply to life sciences and healthcare companies.
Consider Nevada, which grants consumers the broad right to opt out whenever a qualifying ‘operator’ or ‘data broker’ makes their covered information available to others in exchange for money. However, the law exempts numerous categories of information transfer. Disclosures by operators to their service providers and corporate affiliates do not constitute ‘sales’; nor do disclosures that occur as a result of a merger, acquisition, or a bankruptcy.
Even websites with whom the individual has a direct relationship, for purposes of providing a requested product or service – these, too, are exempt from disclosure. This legislative wall intended to protect the consumer is more like a piece of Swiss cheese – not only thin, but full of holes.
(The notable exceptions, of which there are few, are those laws that contain specific consumer protections by way of restrictions on the companies, on the things they can or cannot do, as a result of having sensitive data[5].)
On the upside, these state privacy laws are usually bipartisan; together, we can stand united and ineffectual. But there is a darker side, in that they can limit, delay, or otherwise distort future lawmaking efforts.
Big Value in Big Data
It is nearly impossible to comprehend the full potential value within these data. Many overlapping groups stand to benefit. These are just a handful of the countless ways in which these data are being used already:
- Patients with rare diseases can expect cures to be developed for them more quickly and be rapidly notified of upcoming clinical trials for which they are eligible.
- Patients with multiple co-morbidities can receive more support with care coordination, as well as improved outcomes from a care team data driven approach.
- All patients benefit from secure portals to access their healthcare information, or targeted modules for learning that tie to data driven behavioral nudges.
- Patients whose health is negatively impacted by unrecognized social determinants of health factors may see improved ease of access to community services.
- Researchers will be able to identify what unmet medical needs are most prevalent, and in what populations, in order to target therapeutic development.
- Physicians will have access to clinical care pathway guidance that to improve care delivery for patients with complex diseases.
- Researchers will be able to develop molecular compounds using genomic data and begin to make precision medicine a reality that can be provided at scale.
- Healthcare organizations will enhance efficiency with automation of many simple administrative tasks, such as patient communication, thereby reducing staff burnout.
- Payers can better negotiate on drug prices by being able to quantify the relative value of a therapeutic or different care strategies.
- Payers can target high utilization members with targeted nudge interventions supported by clinical guidelines in better coordination with a member’s care team.
These are critical goals, and they can become our reality, by leveraging these data. Regardless of one’s stance on the appropriate profit margin for a health care provider, a payer, or a life sciences company, the framework that incorporates the distinction between privacy and security – and recognizes a few key attributes inherent to data itself – is the only framework that can offer any exercise of true choice.
Developing plain language to understand and discuss data concepts within the context of privacy choice is a critical action item, and long overdue.
Data has a Multiplicity Problem
Big data has some big regulation challenges. Of critical importance, we cannot consistently verify if data has been deleted. Data has a way of replicating over and over again; it has a multiplicity problem.
When we are moving data, we are actually replicating data. We must ensure deletion was performed in the original location before we can confirm that we have moved the data[6]. Replication is a one step process, but moving is two, so not only do we create more work – but how do you verify that it occurred in every single instance, in every single location, while somehow ensuring no instances of further replication?
This cannot be done. It seems reckless to rely on laws that are fundamentally relying on the honor system of companies.
Data is Relational
Multiplicity is not the only challenge originating from these fundamental attributes. We also cannot consistently verify if there are data in a dataset that are protected health data. Experts argue data only has meaning in a relational sense; that is, the response alone is meaningless without context of the question. Our construct of private health data may have outlived its usefulness in our modern world, at least with respect to how these more recent laws are being written.
Consider that one’s date of birth is PHI when gleaned from a clinical dataset, but that same date of birth collected during the sign-up process for an online account is clearly not. How do you know which one was the sensitive date of birth? Laws being built upon the assumption that we can do such things are fundamentally flawed.
We Cannot Universally Tag Data
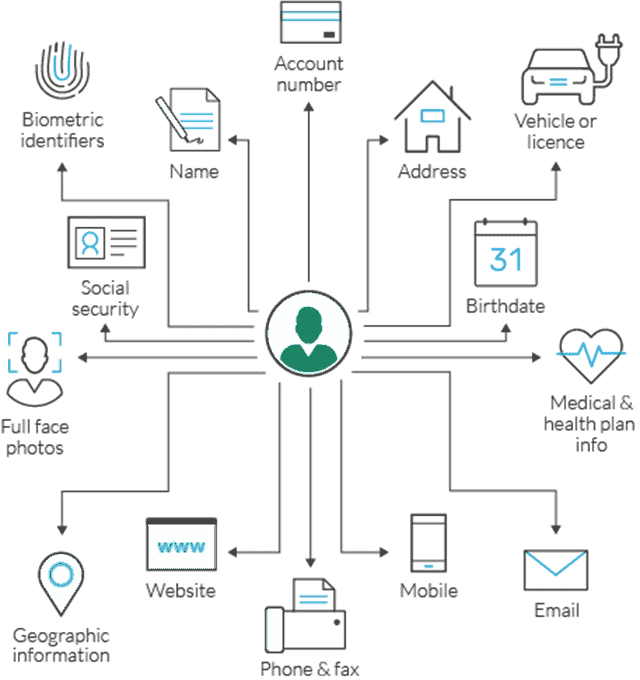
Many of the laws operate on a belief that we can ‘tag’ sensitive data at initial capture. This tiny warning flag will travel with the data goes and we can tell them apart from other data, even if the data point is the same (such as the date of birth example).
However, this does not work. Data do not accumulate lineage information like some type of crust. Someone must build something specific that will do this, for a specific database, and when data are copied out of the structure, the lineage data do not automatically tag along.
Any dataset available from a vendor is going to have data lineage information, but to be clear, this does not mean such data are accurate, nor can one be fully confident that the context of the data was correctly interpreted at the last hand-off. And the ones before that. You get the idea.
Needed: A Better Job Discussing Data Privacy Trade-offs
There are some real-world limitations in our ability to regulate the movement of real-world data. There remains a vast chasm between our reality and that in which much discussion and legislation is being debated.
We are wasting valuable time. The Trusted Exchange Framework and Common Agreement (TEFCA) was passed as part of the 21st Century Cures Act, and the TEFCA framework officially launched in January of this year. Health systems will soon be required to release all electronic health information (EHI) to a patient, or entity acting as a proxy for the patient – such as a health app – upon request.
We must stop debating ethical data uses. Instead, we would be better off directing conversations to the specific trade-offs of data usage and patient control of their PHI. Only then can we build regulations at the federal level, which do not rely on the honor code for enforcement.
[1] https://journalofbigdata.springeropen.com/articles/10.1186/s40537-017-0110-7
[2] https://www.bmj.com/content/377/bmj-2022-070876
[3] https://www.nature.com/articles/s41599-020-00535-6
[4] https://www.ncbi.nlm.nih.gov/books/NBK9576/
[5] https://www.osano.com/articles/data-privacy-laws#:~:text=Despite%20numerous%20proposals%20over%20the,health%20information%2C%20credit%20information%2C%20financial
[6] https://www.nature.com/articles/s41599-020-00535-6




0 Comments